The Cybersecurity and Infrastructure Security Agency (CISA) is a newly formed US federal agency working tirelessly to tackle cyber threats by developing secure and reliable cyberinfrastructure. CISA has warned all the industrial stakeholders in the country to be prepared and to take proactive measures against any malicious cyber activity. Organizations and service providers have been encouraged to have their SHIELDS UP to cyber threats and to take proactive measures to mitigate risk to their networks.

Guidelines Issued by CISA to Avoid Cybersecurity Threats
CISA has set some guidelines necessary to be followed. These mitigation guidelines are briefly explained below:
- It has been made mandatory for each organization to use multi-factor authentication on their systems. This will provide a shield to any phishing activity, making it harder for hackers to get access to information on their systems.
- New technology comes with advanced security features. It is expected that software and applications being used are up to date. This not only minimizes any exploitation due to flaws in older versions, but also enables a strong defense against any attack.
- Despite several security checks, there might still be a chance for malicious activities. Data encryption is the only solution. Companies should make it compulsory to encrypt their data, so that only employees with the correct encryption key can decrypt it.
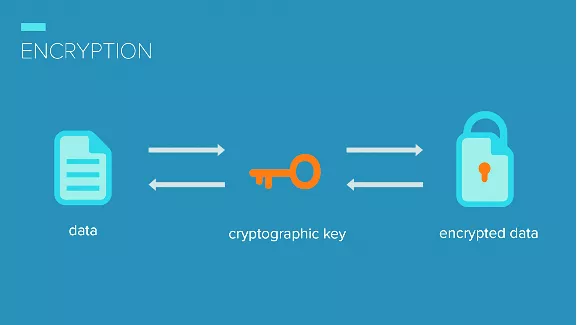
- Data is considered an asset now. According to CISA regulations, there must be multiple data backups online as well as offline.
- In order to get updates about cybersecurity and changes taking place, everyone is requested to sign up for free cyber hygiene services by CISA.
- Organizations have been encouraged to invest in educating their employees about common cyberattack tactics used by attackers over email or through websites, and to report unusual behavior on their computers or phones. More than 90% of such activities start by clicking on an advertisement or opening an email.
Conclusion
Overall, CISA’s Shields Up initiative emphasizes the urgency of proactive cybersecurity measures to protect organizations from evolving threats. By implementing multi-factor authentication, keeping systems updated, encrypting data, maintaining backups, and fostering cybersecurity awareness, businesses can strengthen their defenses against cyberattacks. Staying informed through CISA’s free cyber hygiene services and educating employees on emerging threats will further enhance security, ensuring a resilient cyber infrastructure in an increasingly digital world.
Disclaimer: Any opinions expressed in the blog do not necessarily reflect the opinions of Certrec. The content of this blog is meant for informational purposes only.